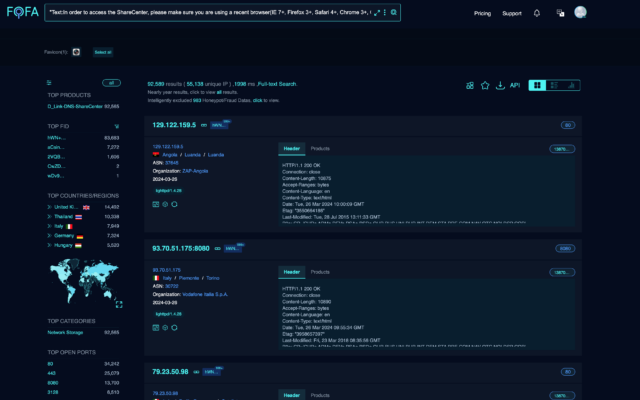
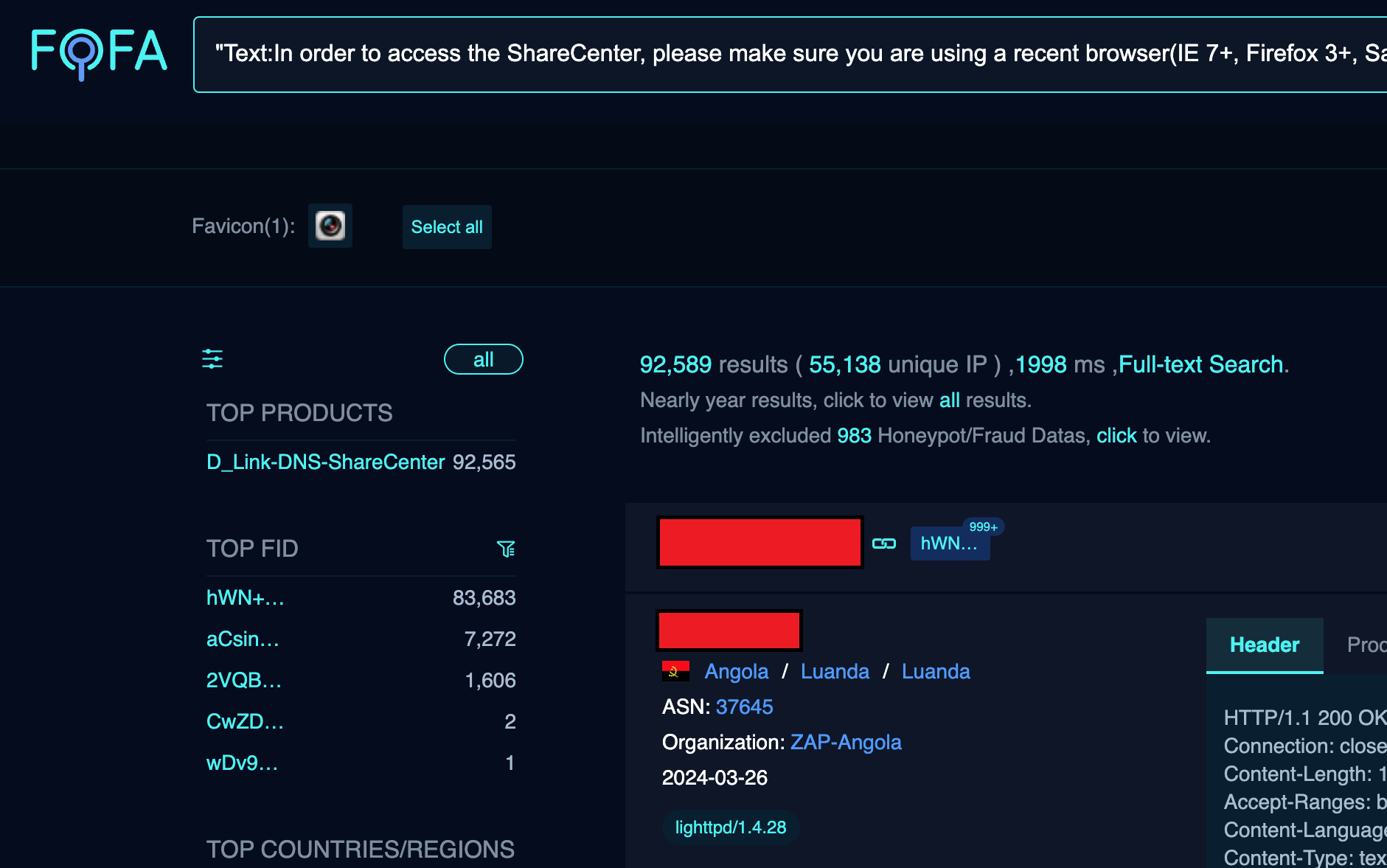
D-Link has recently released a security advisory for 92,000 end-of-life NAS devices that are vulnerable to a critical remote code execution (RCE) zero-day flaw. The vulnerability is the result of a backdoor facilitated through a hardcoded account and command injection issue via the system parameter. Attackers can exploit this vulnerability to remotely take over network-attached storage devices manufactured by D-Link, potentially leading to unauthorized access to sensitive information, modification of system configurations, or denial of service conditions. The researcher who discovered the flaw has disclosed it as CVE-2024-3273 and advises that owners should retire these products and replace them with those that receive firmware updates. D-Link also recommends retiring these devices and replacing them with new ones, but they will not be patching vulnerable NAS devices because they are no longer supported.